The best way to confirm the agents fingerprint at least in Puppet 36 is to run the following command in your agent. Why Fingerprint Identification.
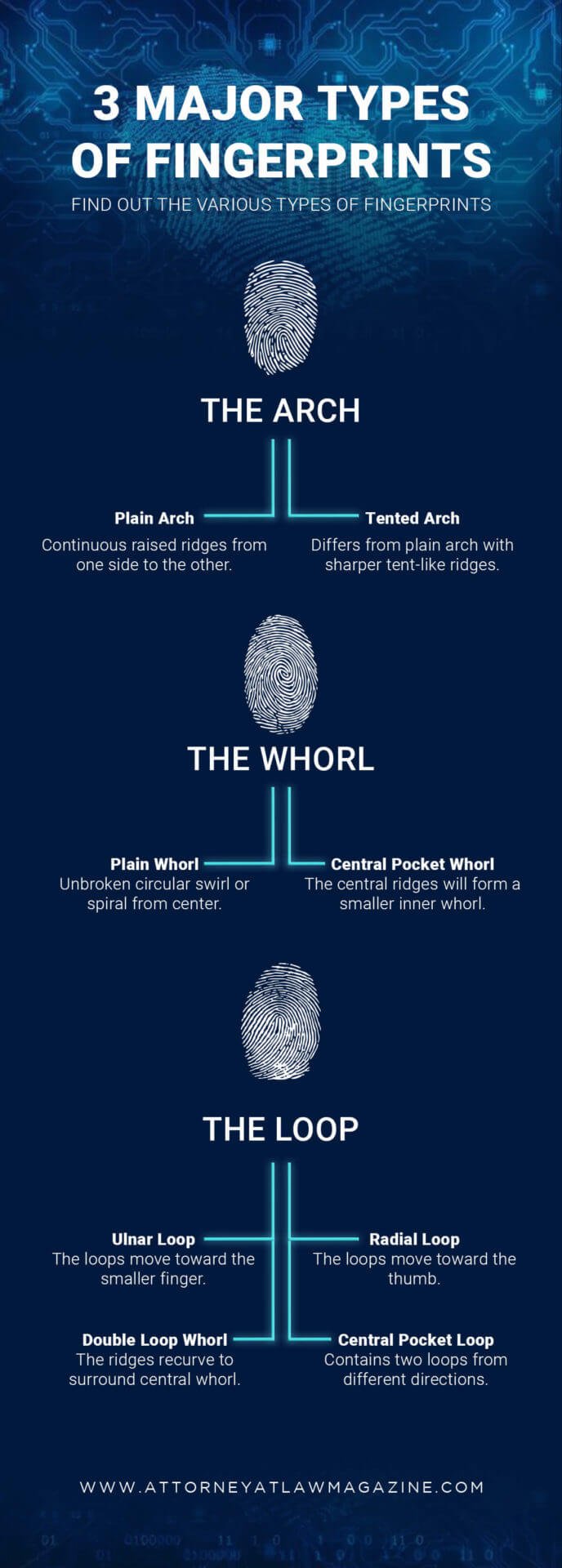
3 Major Types Of Fingerprints Find Out The Various Types Of Fingerprints Attorney At Law Magazine
During the rainy season in most years floodwater drains from several swollen South.
. - minimum path size. On restarting the phone the. BARSKA AX11620 fingerprint safe mini Top Biometric fingerprint gun safes locks are among the latest features to hit the market in this arena.
In the case of the Pixel 6 fingerprint scanner not working at all it seems to be caused when the battery runs out. While conservation areas and indigenous territories have been set up to limit development in parts of the Pantanal the human fingerprint on the landscape is. Find My Device makes it easy to locate ring or wipe your device from the web.
These systems recognize a pre-programmed set of prints. Stylometry is the application of the study of linguistic style usually to written language but it has been applied successfully to music and to fine-art paintings as well. One of the worlds largest freshwater wetlandsthe Pantanalspreads across a bowl-shaped plain where Bolivia Brazil and Paraguay meet.
2048 bits - number of bits set per hash. That is the essential explanation for why fingerprints have replaced other methods of identifying people who are reluctant to admit previous arrests using different names. In this science project you will examine fingerprints from siblings versus pairs of unrelated individuals to figure out if general fingerprint patterns are genetic or random.
Recording an individuals fingerprint pattern manually through a rolling process using ink and a hard fingerprint card. Fingerprint images are digitized through an electronic process enabling the electronic transfer of the fingerprint image data in combination with personal descriptor information to central computers at the DOJ. Like any other method this is not foolproof.
These whorls consist of at least one re-curving ridge or an obstruction at right angles to the line of flow with two deltas and if an imaginary line is drawn in between then no re-curving ridge within the pattern area will be touched or cut. 77 of users began their patterns in one of the corners. 64 bits - target on-bit density 00.
The particular door-mounted scanner tested optically samples the fingerprint and had some extra liveness-sensing features that supposedly looks for pulse body heat and sweat though in the end the door-scanner ended up. This is the simplest form of whorl and also the most common. 2 - minimum fingerprint size.
The default set of parameters used by the fingerprinter is. Best magnetic fingerprint gun safe. 1 bond - maximum path size.
Here are some of the most common lock pattern habits 44 of people usually start their patterns from the top-left corner dot. Images of the ridge endings and bifurcations that make up a fingerprint pattern are stored as images. This is the most popular techniques used in fingerprint attendance system software.
Heat and drought exacerbated fire season in 2020 but cattle grazing and other human activities also primed the region to burn. Puppet agent --fingerprint. The DNA that a person inherits from their parents determines many personal characteristics and traits like whether someone is right- or left-handed or the color of their eyes.
Fingerprint readers take a sample of a fingerprint and match it with an approved-person database. One group of biologists that surveyed the Pantanal soon after the fires estimated that at least 17 million vertebrates were likely killed including millions of snakes rodents and birds. Try to get.
Get common name CN from SSL certificate. Another conceptualization defines it as the linguistic discipline that evaluates an authors style through the application of statistical analysis to a body of their work. The science of fingerprint identification stands out among all other forensic sciences for many.
We would like to show you a description here but the site wont allow us. Have you ever looked at two girls. More details about the algorithm used for the RDKit fingerprint can be found in the RDKit Book.
Replace only after specific pattern How do I write words inside a square root without the words getting italicized. Try this activity again but this time collect fingerprint pattern information from a lot more people to draw a better conclusion about whether fingerprint patterns are inherited. Fingerprints provide a reliable means of personal identification.
7 bonds - fingerprint size. Stylometry is often used to attribute authorship. A common pattern for using a CDN is to set your production application as the origin server.
This means when a browser requests an asset from the CDN and there is a cache miss it will grab the file from your server on the fly and then cache it. Central pocket loop whorl.

Which Ridge Pattern Is The Least Common In Fingerprints Quora

Examples Of Common Fingerprint Patterns And The Determination Of Download Scientific Diagram

Til The Most Common Fingerprint Pattern In The Us Is The Ulnar Loop R Todayilearned
What Is The Most Common Fingerprint Pattern Quora

Measuring The Rarity Of Fingerprint Patterns In The Dutch Population Using An Extended Classification Set De Jongh 2019 Journal Of Forensic Sciences Wiley Online Library


0 comments
Post a Comment